漏洞背景
2020年1月14日微软发布了CVE-2020-0601漏洞公告,此漏洞为Windows加密库中的一个关键的漏洞,Windows CryptoAPI(Crypt32.dll) 验证椭圆曲线加密 (ECC) 证书的方式中存在欺骗漏洞。
攻击者可以通过使用欺骗性的代码签名证书对恶意可执行文件进行签名来利用此漏洞,从而使该文件看似来自受信任的合法来源。美国国家安全局(NSA)已将CVE-2020-0601披露给了Microsoft 。
漏洞详情
crypt32.dll是Windows加密API应用程序接口模块,它提供的Microsoft Windows CryptoAPI无法以正确利用ECC密码术应提供的保护的方式来验证ECC证书。攻击者能够伪造具有受信任根证书颁发机构的证书。
Windows CertGetCertificateChain()函数来确定是否将X.509证书跟踪到受信任的根CA。攻击者可能在易受攻击的Windows系统上欺骗有效的X.509证书链。攻击者甚至可能做到拦截和修改TLS加密的通信或欺骗Authenticode签名。根据NSA成功利用此漏洞将使攻击者能够提供来自受信任实体的恶意代码。其中包含:签名的文件和电子邮件、签名可执行代码等、HTTPS连接。
由于CVE-2020-0601可绕过Windows验证密码信任的功能,因此攻击者可能会将恶意代码或应用传递到用户主机上,使Windows主机面临风险。攻击者可以通过网络钓鱼等诱骗方式使用户受骗安装恶意软件,甚至可以让已中招的设备使用中间人攻击将合法的程序替换为恶意软件,从而部署利用此漏洞的恶意软件。
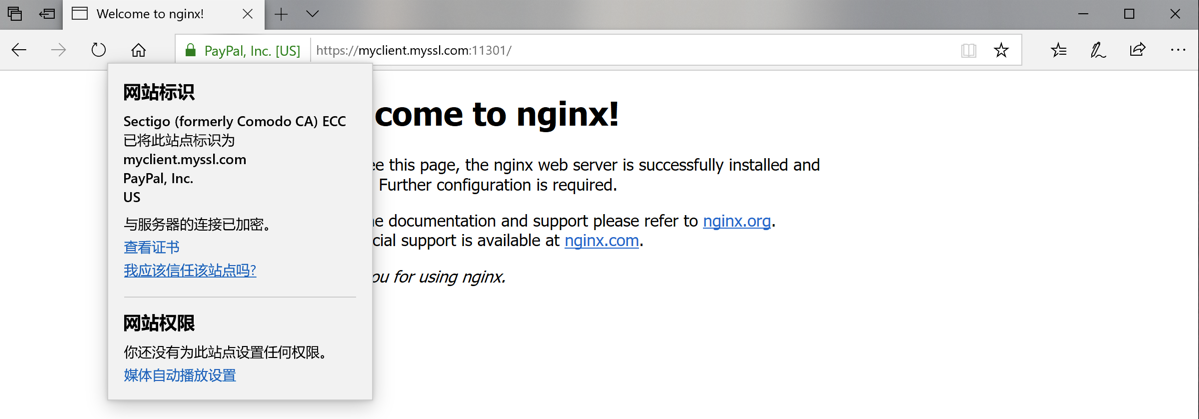
例, 下图为我们利用该漏洞搭建的SSL站点示例:
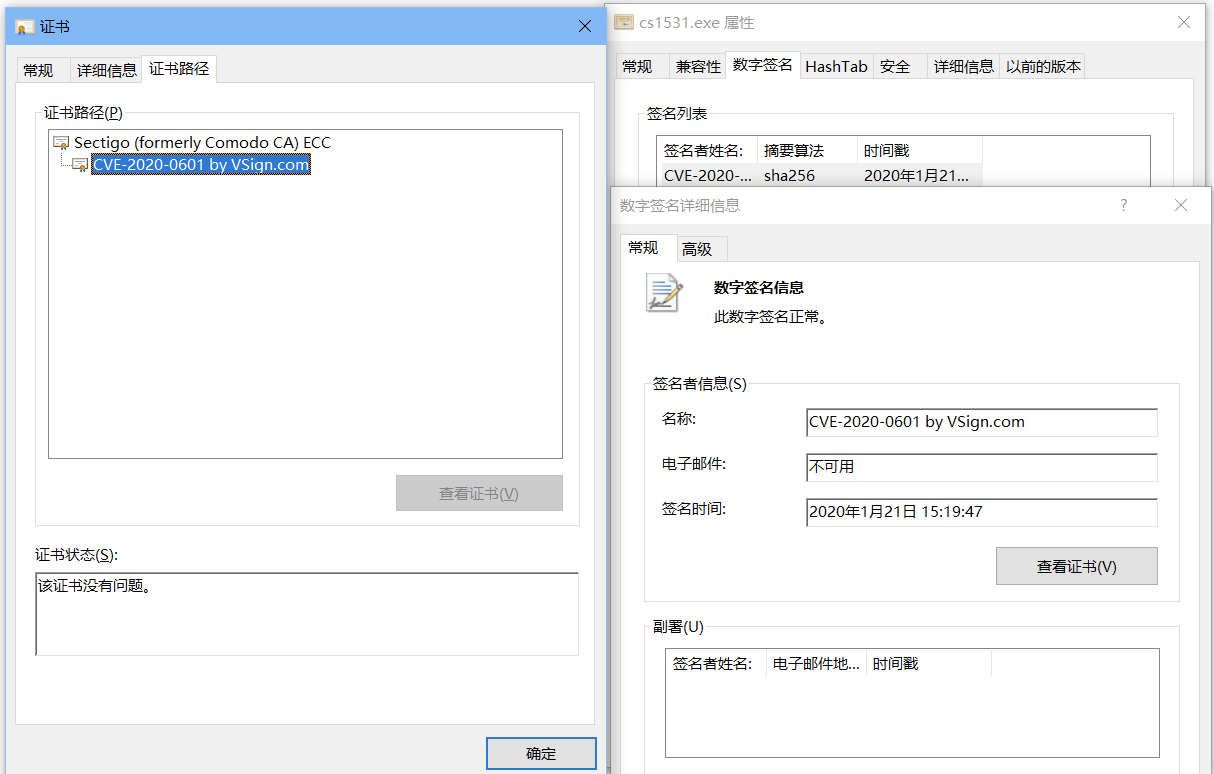
下图为受影响的代码签名示例:
注意:内核驱动签名不受影响,只有普通应用代码签名受影响。
影响版本
- Windows 10 for 32-bit Systems
- Windows 10 for x64-based Systems
- Windows 10 Version 1607 for 32-bit Systems
- Windows 10 Version 1607 for x64-based Systems
- Windows 10 Version 1709 for 32-bit Systems
- Windows 10 Version 1709 for ARM64-based Systems
- Windows 10 Version 1709 for x64-based Systems
- Windows 10 Version 1803 for 32-bit Systems
- Windows 10 Version 1803 for ARM64-based Systems
- Windows 10 Version 1803 for x64-based Systems
- Windows 10 Version 1809 for 32-bit Systems
- Windows 10 Version 1809 for ARM64-based Systems
- Windows 10 Version 1809 for x64-based Systems
- Windows 10 Version 1903 for 32-bit Systems
- Windows 10 Version 1903 for ARM64-based Systems
- Windows 10 Version 1903 for x64-based Systems
- Windows 10 Version 1909 for 32-bit Systems
- Windows 10 Version 1909 for ARM64-based Systems
- Windows 10 Version 1909 for x64-based Systems
- Windows Server 2016
- Windows Server 2016 (Server Core installation)
- Windows Server 2019
- Windows Server 2019 (Server Core installation)
- Windows Server, version 1803 (Server Core Installation)
- Windows Server, version 1903 (Server Core installation)
- Windows Server, version 1909 (Server Core installation)
快速检测
可利用MySSL客户端检测功能快速检测(https://myssl.com/myclient.html), 如果检测到“客户端漏洞“中,CVE-2020-0601为“受影响“,建议按照文末的建议修复。
修复建议
- 开启windows10的自动更新
- 或手动访问官方补丁下载链接下载安装更新包,链接如下
| 系统版本 | 相关文章 | 补丁下载地址 |
|---|---|---|
| Windows 10 for 32-bit Systems | 4534306 | Security Update |
| Windows 10 for x64-based Systems | 4534306 | Security Update |
| Windows 10 Version 1607 for 32-bit Systems | 4534271 | Security Update |
| Windows 10 Version 1607 for x64-based Systems | 4534271 | Security Update |
| Windows 10 Version 1709 for 32-bit Systems | 4534276 | Security Update |
| Windows 10 Version 1709 for ARM64-based Systems | 4534276 | Security Update |
| Windows 10 Version 1709 for x64-based Systems | 4534276 | Security Update |
| Windows 10 Version 1803 for 32-bit Systems | 4534293 | Security Update |
| Windows 10 Version 1803 for ARM64-based Systems | 4534293 | Security Update |
| Windows 10 Version 1803 for x64-based Systems | 4534293 | Security Update |
| Windows 10 Version 1809 for 32-bit Systems | 4534273 | Security Update |
| Windows 10 Version 1809 for ARM64-based Systems | 4534273 | Security Update |
| Windows 10 Version 1809 for x64-based Systems | 4534273 | Security Update |
| Windows 10 Version 1903 for 32-bit Systems | 4528760 | Security Update |
| Windows 10 Version 1903 for ARM64-based Systems | 4528760 | Security Update |
| Windows 10 Version 1903 for x64-based Systems | 4528760 | Security Update |
| Windows 10 Version 1909 for 32-bit Systems | 4528760 | Security Update |
| Windows 10 Version 1909 for ARM64-based Systems | 4528760 | Security Update |
| Windows 10 Version 1909 for x64-based Systems | 4528760 | Security Update |
| Windows Server 2016 | 4534271 | Security Update |
| Windows Server 2016 (Server Core installation) | 4534271 | Security Update |
| Windows Server 2019 | 4534273 | Security Update |
| Windows Server 2019 (Server Core installation) | 4534273 | Security Update |
| Windows Server, version 1803 (Server Core Installation) | 4534293 | Security Update |
| Windows Server, version 1903 (Server Core installation) | 4528760 | Security Update |
| Windows Server, version 1909 (Server Core installation) | 4528760 | Security Update |